How Blockchain Bridges Work: A Comprehensive Explanation
- BLOG
- Blockchain
- October 14, 2025
Moving assets between blockchain networks without a medium can cause delays, failed transactions, or even lost assets. Blockchains like Ethereum, Solana, BNB Chain, etc., can’t directly communicate to transfer assets.
That’s where the blockchain bridge comes in. But how blockchain bridges work?
A blockchain bridge connects two separate blockchains by locking assets on one chain and creating an equivalent on the other. After locking, the bridge verifies the transaction through validators or oracles and then mints an equivalent wrapped token on the destination blockchain.
Want to know what’s really going on behind the scenes? Keep reading, and you’ll learn how the entire process flows.
Contents
- 1 Brief Definition of Blockchain Bridge
- 2 How Blockchain Bridges Work: Core Technologies and Components
- 3 How Blockchain Bridges Work (A Simple Process Flow)
- 4 6 Types of Blockchain Bridge Architectures: How Blockchain Bridges Work Depending on Methods
- 4.1 1. Wrapped Asset Bridges (Lock-and-Mint / Burn-and-Release)
- 4.2 2. Liquidity Pool Bridges (Swap-Based, Not Wrapped)
- 4.3 3. Light Client-Based Bridges (On-Chain Proofs, No Middlemen)
- 4.4 4. Zero Knowledge (ZK) Proof-Based Bridges (Validation Through Cryptographic Proofs)
- 4.5 5. General Message Passing Bridges (Cross-Chain Messaging, Not Just Tokens)
- 4.6 6. Rollup-Based Bridges (L2 to L1, With Proof-Based Finality)
- 5 How Do Security Work in Blockchain Bridge
- 6 How Can Webisoft Help You Connecting Blockchain Bridge
- 7 Conclusion
- 8 FAQs
Brief Definition of Blockchain Bridge
What is a blockchain bridge? A blockchain bridge connects different blockchains, like Ethereum and Solana. It lets users move assets or data between chains that weren’t built to communicate with each other.
Each blockchain operates in its own environment. Therefore, they don’t share the same protocols, so they can’t interact directly. That’s where a bridge acts as a translator.
It locks the original asset on the source chain and creates an equivalent version on the destination chain. The cross chain bridge transfers data without breaking the rules of networks.
How Blockchain Bridges Work: Core Technologies and Components
To understand how blockchain bridges work safely to transfer assets across different blockchains, it’s important to look under the hood. Blockchain bridges rely on a combination of advanced technologies and architectural components, such as:
Primary Technologies Used in Blockchain Bridges
Technologies refer to the systems used to make blockchain bridges function. These are the tools, protocols, or approaches that enable the functionality of a blockchain bridge.
- Smart Contracts: Enable automation of processes like locking, minting, and burning tokens across chains.
- Cryptography (Merkle Proofs, Hash Functions, Digital Signatures): Ensures data integrity and security of cross-chain transactions.
- Zero-Knowledge Proofs (ZK): Verifies cross-chain actions without revealing sensitive information.
- Oracles: Provide off-chain data (e.g., token prices, external events) to blockchains.
- Light Clients: Lightweight versions of blockchains that help verify transactions without needing the full blockchain data.
Primary Components of a Blockchain Bridge & Their Features
Components are the specific building blocks or pieces of software that implement or carry out the technologies. These are the actual parts of the infrastructure that work together to achieve the end goal.
| Component | Feature |
| Bridge Contract | Automates the entire bridging process, ensuring tokens are locked, minted, and burned. |
| Merkle Trees | Verifies data integrity and ensures that transactions are accurate and complete across chains. |
| Signature Validators | Authenticate and validate transactions, ensuring security and preventing fraud. |
| Multi-Signature Wallets | Ensures additional security by requiring multiple approvals for a transaction to be completed. |
| ZK-Bridge Proofing | Uses zero-knowledge proofs to verify the legitimacy of transactions without revealing details. |
| Price Feed Oracles | Provides necessary external data (like token prices) that influence transaction validity. |
| Layer 2 Bridges | Enable scaling by moving execution off-chain while ensuring settlement security on Layer 1. |
| Sharding Mechanisms | Distributes data across smaller pieces (shards) to improve speed and scalability in cross-chain operations. |
| Ethereum Light Client | Verifies the state of Ethereum on a different chain to ensure trustless and decentralized validation. |
How Blockchain Bridges Work (A Simple Process Flow)
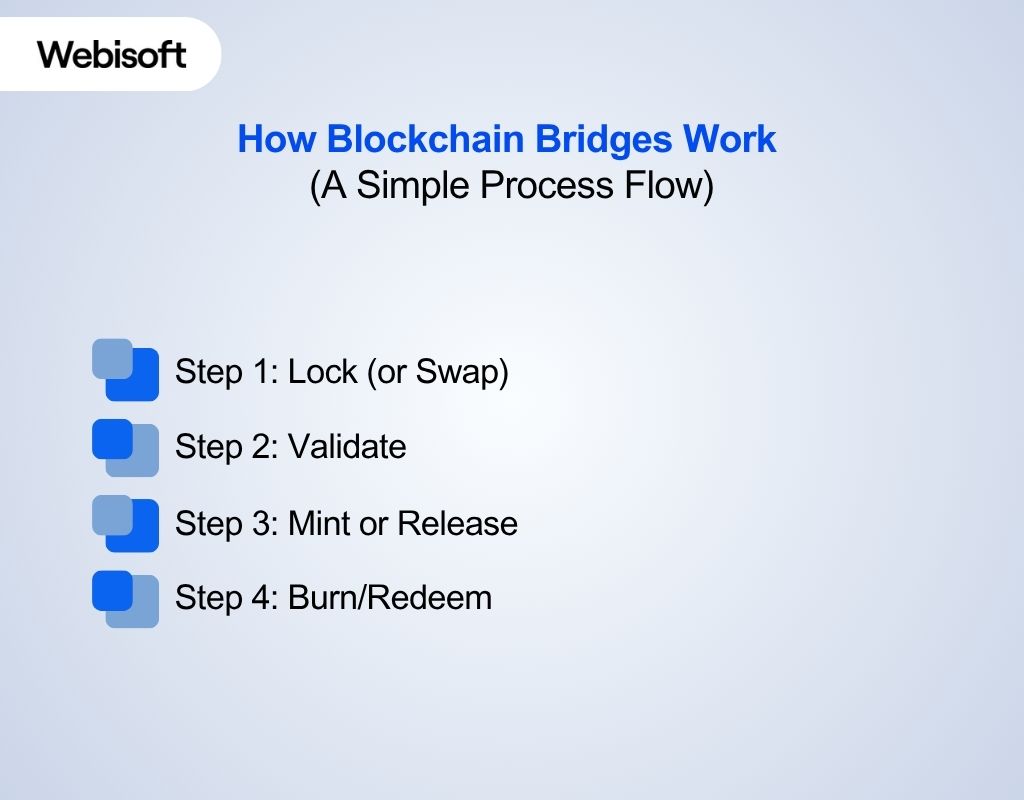
Building blockchain bridges makes it easy to move tokens from one blockchain to another. Here’s the basic working process of blockchain bridges explained for beginners:
Step 1: Lock (or Swap)
When you want to move assets across blockchains, the first thing that happens is that the asset gets locked in a smart contract. Here’s how the locking process works:
- You begin by sending your asset (for example, 1 ETH) to the bridge contract on the source blockchain.
- The bridge contract on the source chain locks the original asset in place. This means the asset is held securely within the contract and is no longer under your control for the time being.
- The contract creates a record or proof that the asset is locked. This proof is crucial for ensuring the transaction can proceed smoothly.iiiii
- The asset is now locked in the smart contract, and the bridge has confirmed that the token is safely stored and ready to be bridged to the destination chain.
Step 2: Validate
Once the asset is locked on the source chain, the next step is validation. This is how the bridge ensures the transaction is legitimate before proceeding. The validation process is as follows:
Transaction Monitoring:
The bridge starts by monitoring the blockchain for the transaction. It could be through a validator node or oracle that checks the transaction’s details (such as the amount of the asset, sender, and destination address).
Cross-Chain Proof Generation:
The bridge creates proof that the locked token exists and has been confirmed on the source chain.
This could involve a Merkle proof or digital signature methods that allow the bridge to prove that the transaction happened without exposing sensitive data.
Validators Check the Source Blockchain:
Validators (either centralized or decentralized) verify the transaction on the source blockchain. They check the block height, transaction hash, and other details to ensure the asset is locked correctly and the transaction is valid.
Consensus & Confirmation:
Once the validator confirms the transaction’s legitimacy, it’s passed along to the bridge system. Validators typically reach a consensus on whether the transaction is correct, ensuring there are no malicious or faulty data.
Signal Sent to Destination Chain:
Once validated, the bridge signals to the destination chain that the transaction is verified and ready for minting or asset transfer. Only after validation can the asset move to the next step.
Step 3: Mint or Release
Once a bridge transaction is validated, the bridge performs two key actions: minting the equivalent token on the destination chain and releasing the original token on the source chain. Here’s how each step happens:
1. Minting the Wrapped Token on the Destination Chain
After the transaction is validated, the bridge mints a new token on the destination chain. This wrapped token represents the asset you locked on the source chain.
- How it works:
- A smart contract on the destination chain (e.g., Solana) is triggered by the bridge to mint an equivalent version of the asset (like wETH if you sent ETH from Ethereum).
- This minted token is backed 1:1 by the token you locked on the source chain. So, if you locked 1 ETH on Ethereum, the bridge mints 1 wETH on Solana.
- Why minting?
Minting is necessary because the destination chain needs a native token that can be used within its ecosystem. The minted wrapped token acts as a placeholder, representing the original token while following the rules of the destination blockchain.
2. Releasing the Original Token on the Source Chain
The original token (like ETH) stays locked in a smart contract on the source chain (like Ethereum) until you burn the wrapped version on the destination chain.
- How it works:
- The bridge smart contract on the source chain holds the token securely.
- When you’re ready to move it back, you send the wrapped token (wETH) to the bridge on the destination chain. The bridge burns it. Only after that burn is confirmed does the source chain release the original token back to your wallet.
- Why release?
This keeps the system fair and secure. You can’t have the same value on two chains at once. Burning before releasing makes sure the total supply stays balanced. That’s how the bridge maintains a 1:1 relationship.
Step 4: Burn/Redeem
When you’re ready to return your asset from the destination chain back to the source chain, the process works in two parts: burning the wrapped token and redeeming the original token.
1. Burn the Wrapped Token on the Destination Chain
- When you’re ready to redeem your tokens, you send the wrapped token (like wETH) on the destination chain back to the bridge’s smart contract.
- The smart contract then burns the wrapped token. This means it destroys or removes the token from circulation on that chain.
- Why burn? Burning ensures that the total supply of wrapped tokens never exceeds the original asset locked on the source chain.
2. Redeem the Original Token on the Source Chain
- After burning the wrapped token, the bridge’s smart contract on the destination chain sends a confirmation to the bridge on the source chain (in this case, Ethereum).
- The bridge on Ethereum then releases the original token (ETH) back to your wallet on Ethereum.
- This step ensures that the total supply of the original asset is preserved and no tokens are duplicated during the cross-chain transfer.
6 Types of Blockchain Bridge Architectures: How Blockchain Bridges Work Depending on Methods
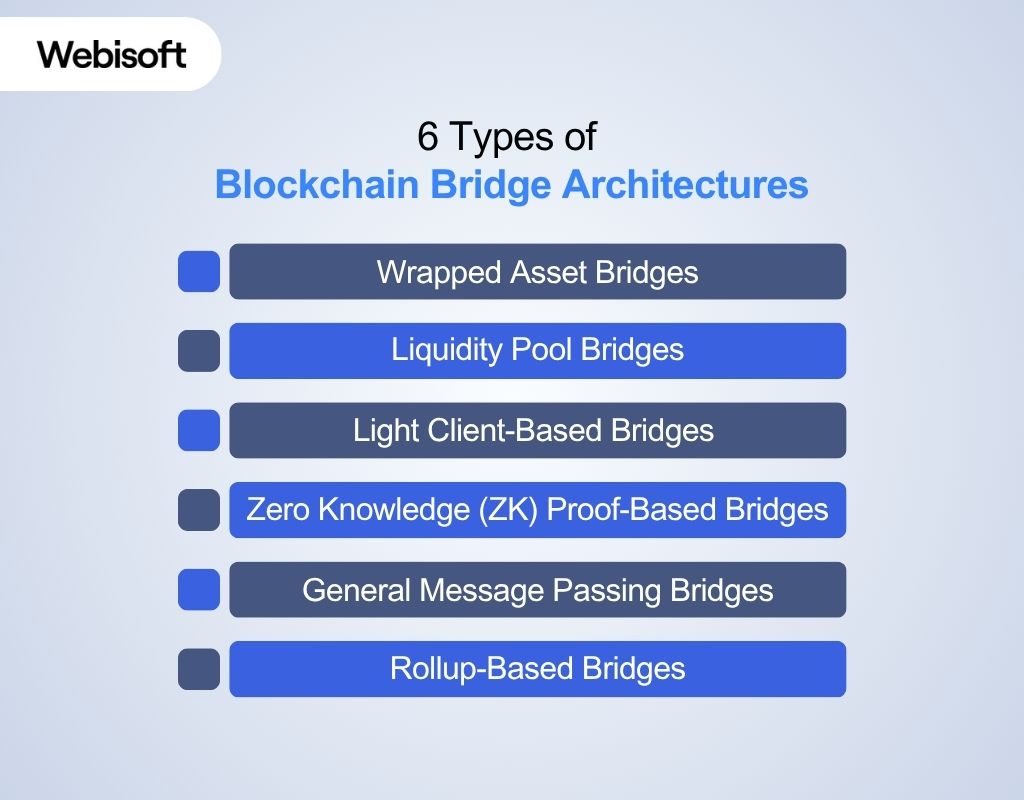
There are different functional types of blockchain bridges, and not all of them work in the same flow. Here’s how they differ in working process depending on the types of underlying mechanisms:
1. Wrapped Asset Bridges (Lock-and-Mint / Burn-and-Release)
Wrapped asset bridges lock tokens on the source chain and mint wrapped versions on the destination.
It’s used by Wormhole, Anyswap, and Multichain; they follow the standard flow.
But validation depends on external validators or relayers, not cryptographic proof. If that trust layer fails, users are stuck. There’s no automatic fallback or built-in recovery mechanism.
How It Works
- You lock a token (like ETH) in a smart contract on Chain A.
- The bridge mints a wrapped version (like wETH) on Chain B.
- To reverse it, you burn the wrapped token on Chain B and unlock the original token on Chain A.
How the Working Flow Differs
The flow looks identical to the standard model, but the validation is off-chain and centralized. Validators or oracles confirm the lock event and trigger the mint. That external trust layer is the single point of risk.
2. Liquidity Pool Bridges (Swap-Based, Not Wrapped)
Liquidity bridges skip wrapping entirely. Instead, they use token pools on both chains to perform real-time swaps. You send tokens into a pool on Chain A and get equivalent assets from a pool on Chain B.
This model powers fast, low-latency bridging in platforms like Synapse, Hop Protocol, and Across. The trade-off? It only works when there’s enough liquidity on both ends. If the pool dries up, you’re out of luck.
How It Works
- You deposit tokens into a liquidity pool on one chain.
- A matching token is pulled from the bridge’s pool on the destination chain.
- No wrapping, no minting, just a swap.
How the Working Flow Differs
There’s no lock or mint step. You’re not interacting with a wrapped token system; you’re trading directly across pools. Validation is simple balance-checking, not proof-based, and there’s no burning involved on the return.
3. Light Client-Based Bridges (On-Chain Proofs, No Middlemen)
These bridges keep the standard flow but do it without relayers or off-chain validators. Instead, they use a light client that runs on the destination chain and independently verifies source-chain data.
Cosmos IBC, Near’s Rainbow Bridge, and Ethereum Beacon-based bridges follow this model. It’s trustless, but not cheap, and definitely not fast.
How It Works
- Tokens are locked on the source chain.
- A light client on the destination chain checks the lock using Merkle proofs.
- Once verified, a wrapped token is minted.
- To redeem, the burn is also verified by the light client.
How the Working Flow Differs
The flow remains lock → validate → mint → burn, but validation is done entirely on-chain. That removes reliance on third parties, no relayers, no multisigns, but increases computational cost and complexity.
4. Zero Knowledge (ZK) Proof-Based Bridges (Validation Through Cryptographic Proofs)
Application of ZK proofs swaps out traditional validation for math. Instead of watching events on the source chain, they generate a zero-knowledge proof that something happened, then verify that proof on the destination.
Projects like zkBridge, Succinct Labs, and Herodotus are leading this model. It’s lightweight and secure but hard to build and not widely deployed yet.
How It Works
- Tokens are locked on the source chain.
- A ZK proof is generated off-chain confirming the lock.
- The destination chain verifies the proof before minting.
- On the return, a burn action generates a new proof to release the original.
How the Working Flow Differs
The process still hits all four steps, but the key change is in validation. No one watches the chain; a proof speaks for itself. It eliminates the need for trusted validators but introduces complexity in proof generation and setup.
5. General Message Passing Bridges (Cross-Chain Messaging, Not Just Tokens)
GMP bridges aren’t focused on assets. They move messages, like smart contract calls or governance instructions, across chains.
It’s used by LayerZero, Axelar GMP, and Wormhole’s core messaging layer, these bridges unlock true composability. But they operate outside the lock/mint model entirely.
How It Works
- You send a structured message from Chain A.
- The bridge verifies the message (often with relayers or oracles).
- The destination chain executes the action (like triggering a contract).
- There’s no token creation or redemption involved.
How the Working Flow Differs
This model doesn’t use lock, validate, mint, or burn. Instead, it processes and delivers logic. It’s a different category altogether, built for dApps that need communication across chains, not just asset transfer.
6. Rollup-Based Bridges (L2 to L1, With Proof-Based Finality)
These bridges are native to the Ethereum ecosystem. They connect Layer 2 networks like Optimism and Arbitrum back to Ethereum using fraud proofs (for optimistic rollups) or ZK proofs (for zk-rollups). The architecture sticks to the standard flow but applies it in batches with built-in delays.
How It Works
- Assets are locked on L2.
- A batch of transactions is posted to L1.
- L1 verifies the batch using a fraud or ZK proof.
- Once confirmed, assets are released or made claimable.
How the Working Flow Differs
Validation doesn’t happen per transaction; it’s aggregated. Withdrawals take longer on optimistic rollups due to challenge periods. ZK rollups are faster but need specialized proof systems. The flow is intact but stretched out in time and scale.
How Do Security Work in Blockchain Bridge
Blockchain bridging has many risks, and they usually come from:
- Over-trusting validators
- Poor smart contract design
- Lack of fallback plans
You’re trusting a system to move assets between two blockchains that don’t trust each other. So, how blockchain bridges enable token transfers along with other assets with blockchain bridge security? Let’s break it down:
Step 1: Trusting the Lock
First up, when you move tokens from one chain to another, the bridge has to “lock” your token on the source chain. If the contract that locks your token is buggy or can be bypassed, you could lose everything before anything even happens on the second chain.
Security here depends on:
- Bug-free smart contracts
- Strict access controls, only the bridge should touch those tokens
- Fail-safes to prevent accidental unlocking
Step 2: Proving Something Happened
When you lock a token on Chain A, the bridge has to prove to Chain B that the lock event was real, valid, and irreversible. Only then does Chain B mint a wrapped version.
The bridge sends a validated message or proof to a smart contract on Chain B, which triggers minting or release actions. But the second chain can’t see the first chain directly. That’s where validation models come in. There are a few ways bridges pull this off:
- Some rely on validators or relayers
They act as witnesses and tell the second chain, “Yep, that happened.” The problem is what if those validators get hacked or go rogue? Poor data gets passed through.
- Others use light clients
They verify source chain transactions by maintaining a minimal trustless client of essential headers. These are more secure but also heavier and slower.
- Using ZK Proofs
ZK proofs are cryptographic evidence that an event happened; no guesswork is needed. But they’re tough to build and still pretty rare in live bridges.
Step 3: Who’s Watching the Watchers?
Even if you’ve got great code and strong validation logic, there’s still one big issue: Who’s in charge of the bridge?
Some bridges are completely centralized. A single company or multisig wallet holds all the power. That’s fast and efficient but also fragile. If that one group gets compromised or makes a mistake, the whole bridge fails.
Others are more decentralized, a network of validators, or even fully trustless systems running on smart contracts. These are harder to break but also slower and more complex.
Step 4: When Things Go Sideways
Smart bridges aren’t just built to succeed; they’re built to survive failure. A good bridge for added security will include:
- Pause functions if something sketchy happens
- Alert systems to warn users of issues
- Recovery plans, such as “can the system roll back or halt without needing a human to jump in?”
Unfortunately, many of the biggest hacks happened because these tools were missing or nobody acted fast enough.
How Can Webisoft Help You Connecting Blockchain Bridge

Webisoft offer the foundational tools of blockchain needed to build one. That means if you’re planning to integrate a blockchain bridge into your ecosystem, Webisoft can help in multiple steps, such as:
Smart Contract Development
Bridges rely on smart contracts to lock, mint, burn, and release tokens. Webisoft specializes in secure smart contract creation and audits, the exact building blocks required for a safe, on-chain bridge.
Blockchain Consultancy
Webisoft offers blockchain consultancy, which can guide you through key architectural decisions, including wrapped asset design and token logic (ERC-20/NFT compatibility).
They also give you ideas on how to structure your bridge to fit your business needs. While they don’t handle token development directly, they can help you define what’s needed.
dApp Development
Blockchain bridges often require a front-facing dApp development for users to interact with.
Webisoft has deep experience in building full-stack blockchain applications, meaning they can help design and deploy the interface your bridge needs, from Web3 wallet connection to bridge dashboards.
Public/Private Blockchain Integration
If you’re building a cross-chain system that connects public networks like Ethereum, Webisoft can help with integration. They also offer deployment support for private or permissioned blockchains.
Talk to Webisoft and let them help you build the foundation for a secure, scalable blockchain-powered system.
Conclusion
To sum up, how blockchain bridges work? Blockchain bridges act as secure translators between different blockchains, enabling tokens and data to move across networks that normally can’t talk to each other.
They lock assets on one chain and unlock or mint equivalents on another, powered by smart contracts, validators, and sometimes oracles.
Understanding how blockchain bridges work enables secure cross-chain apps, wrapped assets, and decentralized ecosystem access. Book a quote for further consultancy with Webisoft!
FAQs
Here are some commonly asked questions regarding how blockchain bridges work:
How secure are blockchain bridges?
Blockchain bridges can be vulnerable to hacks if poorly designed. Security depends on smart contracts, validator trust, and audits. Past incidents (e.g., Ronin, Wormhole) highlight the risks.
Why use a bridge instead of a centralized exchange?
Bridges let you transfer assets directly between blockchains without intermediaries, keeping control of your funds and avoiding exchange fees, delays, or KYC requirements common with centralized platforms.
Do blockchain bridges create new tokens on the destination chain?
Yes, most blockchain bridges create “wrapped” tokens on the destination chain. These tokens represent the original assets locked on the source chain and are pegged 1:1 in value.
