In this technology-dominated age, deceitful activities have shown a notable surge. This makes the establishment of robust security measures paramount, especially in the context of transactional operations.
While blockchain has emerged as a game-changing solution, it requires additional security layers to safeguard transactional integrity. This is where Zero Knowledge Proof (ZKP) comes into play.
From the get-go, cryptography has held a solid link to the blockchain. Yet, the union of blockchain and cryptography has caught everyone’s attention, specifically following the advent of ZKP.
These cryptographic strategies offer thorough security for blockchain-based transactions, paving the way for a safe medium for financial operations.
Contents
- 1 What is Zero-Knowledge Proof?
- 2 Types of Zero-Knowledge Proof in Blockchain Projects
- 3 Delving into Zero-Knowledge Proof in the Tech Sphere: Spotlight on Zcash
- 4 Applications of Zero-Knowledge Protocol on the Blockchain
- 5 Advantages of Zero-Knowledge Proof
- 6 Applications of Zero-Knowledge Proof
- 7 Blockchain Development Service Of Webisoft
- 8 Endnote
- 9 Frequently Asked Questions
- 9.1 How Does Zero-Knowledge Proof Enhance Blockchain Security?
- 9.2 What Are Some Practical Use Cases for Zero-Knowledge Proofs in Blockchain?
- 9.3 Can You Provide an Example of Zero-Knowledge Proofs in a Blockchain Scenario?
- 9.4 Are There Any Limitations or Challenges Associated with Zero-Knowledge Proofs in Blockchain?
What is Zero-Knowledge Proof?
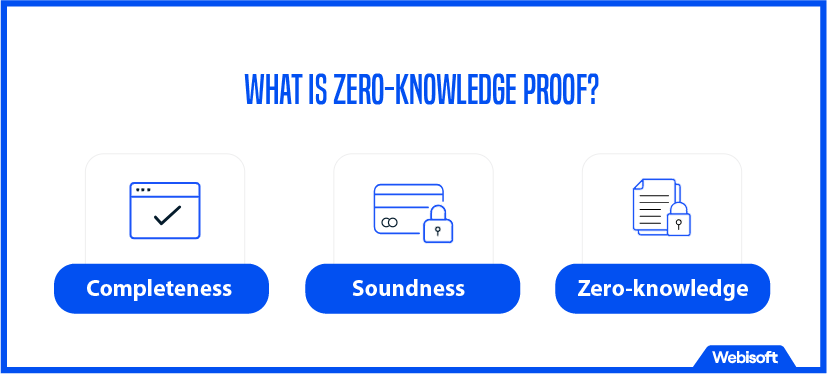
Zero-Knowledge Proof (ZKP) is a cryptographic protocol that maintains the utmost privacy during transactions. It restricts the information exchange to only a known value between the involved parties, the prover, and the verifier.
The critical aspect of ZKP is its ability to allow individuals to validate their knowledge about a specific value without revealing any extra information.
ZKPs are defined by three fundamental attributes:
- Completeness: This property serves as the green light for the transaction. It enables the prover to proceed if the transaction assertion is accurate. In the event of a truthful statement, the verifier holds the power to authorize the prover to continue with the proposed inputs.
- Soundness: This attribute is responsible for maintaining the transaction’s integrity. It certifies that the transaction is free from any illegitimate activities. Should the transaction be false or misleading, the verifier remains unconvinced.
- Zero-knowledge: This property confines the verifier’s knowledge to only the statement’s validity. Any other potentially sensitive or private information remains concealed from the verifier.
The formulation of a Zero-Knowledge Proof encompasses a series of steps that the prover must undertake when they possess all the requisite information. Should there be an error, the verifier’s check can detect it with a high level of probability.
Types of Zero-Knowledge Proof in Blockchain Projects
Zero-Knowledge Proofs (ZKPs), cryptographic tools that provide a layer of privacy in transactions, can be categorized into two fundamental types.
These include Interactive ZKPs and Non-Interactive ZKPs, each with unique characteristics and ways of functioning.
1. Interactive ZKP Or Interactive Zero-Knowledge
This form of ZKP incorporates concepts rooted in mathematical probability. In an interactive ZKP, the role of the prover is to convince a specific verifier about the truth of a particular fact.
This proofing process is not a one-time event but needs to be carried out repeatedly for each verifier involved in the transaction. It might seem like an intensive process. But ensuring that each verifier independently validates the prover’s claim is essential.
The essence of an interactive ZKP lies in the series of steps that the prover has to undertake. These actions are designed to demonstrate their knowledge of a secret value or fact without explicitly revealing it.
The verifier challenges the prover at each step, who then responds based on their knowledge.
The responses must consistently align with the original claim for the verifier to accept the proof. This back-and-forth continues until the verifier is convinced or the prover fails to prove their claim.
2. Non-Interactive ZKP
Contrary to its interactive counterpart, non-interactive ZKPs eliminate the need for direct interaction between the verifier and the prover.
In this case, the prover produces proof that can be independently verified by anyone at any time, with the verification process being able to take place at a later stage.
This feature allows for a more streamlined and efficient verification process, removing the need for each verifier to be present or engaged in an interactive session with the prover.
In the non-interactive ZKP model, the prover uses specific software to generate a proof. This proof includes a commitment to the secret value or fact, a challenge created through a deterministic function, and a response that satisfies the challenge.
Since the challenge is determined by itself rather than a verifier, the need for direct interaction is bypassed. Any verifier can then use the same deterministic function and the given proof to verify the prover’s claim independently.
Each type of ZKP has its benefits and drawbacks. Interactive ZKPs, while being more robust due to the involvement of each verifier, can be time-consuming and resource-intensive.
On the other hand, non-interactive ZKPs, though efficient and convenient, rely heavily on the robustness of the software used to create the proof.
In cryptography, both interactive and non-interactive ZKPs play vital roles in maintaining the integrity of transactions. Understanding their differences can help us appreciate the level of security they bring to the digital world.
Delving into Zero-Knowledge Proof in the Tech Sphere: Spotlight on Zcash
In the realm of technology, Zero-Knowledge Proof (ZKP) finds its implementation in various applications, with Zcash as a flagship example. Zcash is noteworthy as it marks the debut use of zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge). It is a crucial variant of Zero-Knowledge cryptography.
Zcash employs zk-SNARKs to establish an extra layer of privacy for its transactions. This technology enables the blockchain to maintain a secure ledger of balances without disclosing the parties or amounts involved in transactions.
Zcash provides the luxury of transparency where it’s needed while guaranteeing privacy where desired.
The functionality of zk-SNARKs revolves around three core algorithms:
1. Key Generator
The critical generator’s role involves setting parameters for creating a key pair. A trusted entity generates a private and public key pair, then eliminates the private data post-generation.
This process results in a new key pair generated from the public data. One of these keys serves the purpose of proving. The other is used for verification. This method upholds the trust and integrity of the transaction by ensuring that the keys are generated from a secure source.
2. Prover
The prover’s task begins when they receive the proving key. Their goal is to substantiate their knowledge without revealing any extra information. The prover validates the private key and communicates the statement forward.
Here, the prover’s ability to convince the verifier without giving away any information forms the core of the Zero-Knowledge principle.
3. Verifier
The verifier is responsible for receiving input from the prover and confirming the truthfulness of the statement. The verifier uses the verification key to ensure that the prover’s statement aligns with the original claim. Thereby ascertaining the legitimacy of the transaction.
zk-SNARKs also abide by four essential properties to ensure a secure and efficient transaction:
- Succinctness: The verifier should learn nothing beyond the validity of the statement. Challenges to the prover should execute swiftly, ideally within a few milliseconds, to maintain the efficiency of the transaction.
- Non-Interactivity: The process should not necessitate voluntary interaction between the prover and the verifier, as this could compromise the speed and simplicity of the transaction.
- Soundness: The proof must uphold the principles of soundness with zero-knowledge encryption. This ensures that a fraudulent statement cannot be presented as true, safeguarding the transaction’s integrity.
- Reliance on a Trusted Witness: The prover and verifier cannot proceed without a trusted third-party or witness. This witness must confirm the initial statement’s truthfulness to prevent any potential fraudulent activity.
Zcash’s implementation of zk-SNARKs illuminates the potential of Zero-Knowledge Proofs in enhancing the security and privacy of transactions.
This technology underscores how Zero-Knowledge cryptography can offer a balance of transparency and privacy, presenting a promising future for secure transactions in the digital world.
Applications of Zero-Knowledge Protocol on the Blockchain
Zero-Knowledge Proof has several use cases in the realm of blockchain:
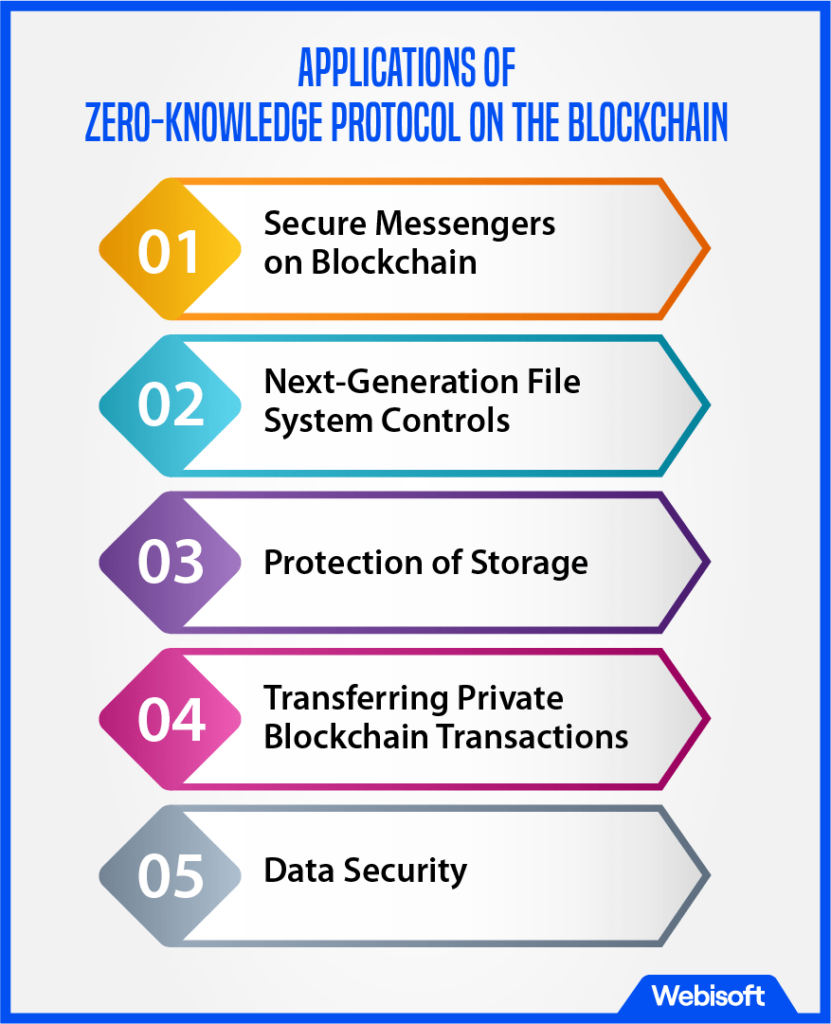
- Secure Messengers on Blockchain: While current messengers promise encryption, an unencrypted blockchain could revolutionize secure messaging. By combining ZKPs and blockchain, a robust and secure messenger platform can be created.
- Next-Generation File System Controls: ZKPs can add multiple layers of security to files and logins, making it challenging for hackers to alter or retrieve data.
- Protection of Storage: ZKPs provide a security protocol for information stored, ensuring formidable safeguards and a highly secure environment.
- Transferring Private Blockchain Transactions: Integrating ZKP with private blockchain transactions can eliminate numerous loopholes present in conventional procedures, resulting in a powerful hacker-proof process.
- Data Security: Sensitive data controllers, such as banks and hospitals, can ensure data remains inaccessible to third parties by leveraging ZKPs and blockchain.
With Zero Knowledge Proof, the future of secure transactions and data protection looks promising. Its seamless integration with blockchain technology has the potential to transform various industries, ensuring confidentiality and integrity every step of the way.
Advantages of Zero-Knowledge Proof
Zero-Knowledge Proofs (ZKPs) offer an ingenious solution to maintaining privacy in an interconnected world. By validating data without revealing it, ZKPs uphold data security, enhance privacy, and strengthen trust in blockchain transactions and beyond.
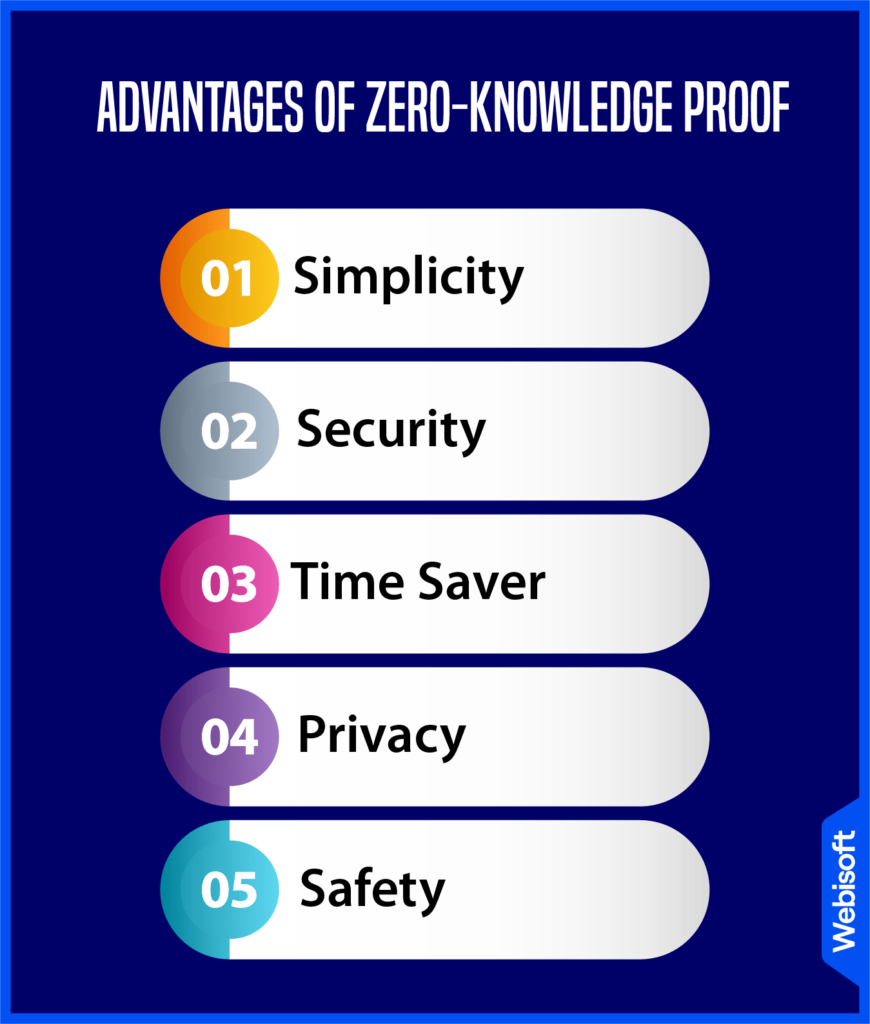
Simplicity
One of the key advantages of ZKPs is their simplicity. It doesn’t require any specialized software knowledge to operate, making it accessible to users from all backgrounds.
Despite its simplicity, ZKPs offer powerful solutions that have a significant impact on our daily lives. Furthermore, ZKPs provide a balance between encryption and security, offering the best of both worlds seamlessly.
Security
ZKPs excel in terms of information-sharing security. Users can confidently utilize ZKPs without needing to understand complex codes or analytics.
Time Saver
ZKPs streamline blockchain transactions, reducing the time required for processing. This time-saving attribute brings added value to users’ experiences.
Privacy
Safeguarding user privacy is a highly valued characteristic of ZKPs. It eliminates the need for sharing sensitive data, ensuring a high level of privacy.
Safety
Users appreciate ZKPs for their ability to protect their data. With ZKPs, users have control over sharing data and can avoid companies that request access to personal information without a valid reason.
Applications of Zero-Knowledge Proof
In addition to its use in blockchains like ZCash, Zero-Knowledge Proof finds application in various scenarios:
1. Decentralized Oracle Networks
These networks provide off-chain data to smart contracts and can utilize ZKPs to share certain facts about the off-chain data without compromising the on-chain information.
DECO, a privacy-controlled oracle protocol within Chainlink’s network, uses ZKPs to ensure data privacy and tamper-proofing. By extending HTTPS/TLS protocols, DECO allows for secure data transfer without requiring special hardware or server-side changes.
2. Decentralized Identity Protocols
Platforms like CanDID, powered by ZKPs, enable users to retrieve their information and credentials without relying on third parties.
These credentials, signed by authoritative issuers, connect claims with users, such as citizenship, occupation, and educational qualifications.
DECO facilitates existing web servers to act as issuers, employing key-sharing management for privacy and Sybil resistance. Unique identifiers like Social Security Numbers (SSNs) enhance privacy and data security.
3. Monetization of Proprietary and Sensitive Datasets
DECO empowers traditional institutions and data providers to monetize their proprietary and sensitive datasets with confidentiality.
Rather than posting all data on-chain, these service providers can use attestations accessed through ZKPs to prove facts about the data they intend to publish.
This approach creates a new market for data providers to increase their dataset revenue while ensuring zero data leakage.
Blockchain Development Service Of Webisoft
Webisoft stands at the forefront of technological innovation, pushing boundaries in the arena of blockchain development.
This pioneering tech firm has carved out a unique position in the rapidly evolving landscape of blockchain technology. We offer groundbreaking solutions tailored to specific business needs.
Capitalizing on its deep-seated knowledge and experience, Webisoft crafts robust, scalable, and highly secure blockchain applications. They harness the power of distributed ledger technology, embodying the principles of decentralization and transparency.
Webisoft’s dedicated team of blockchain developers showcases proficiency in several blockchain platforms and languages. They are adept at creating custom smart contracts, decentralized applications (DApps), and cryptocurrency wallets.
Moreover, their expertise extends to developing secure, immutable, and efficient blockchain systems for diverse sectors, such as finance, healthcare, and supply chain management.
In the realm of blockchain consultation, Webisoft takes a proactive approach. Their consultants work closely with clients, offering insights into how blockchain can transform their business model.
They provide end-to-end guidance, from ideation and strategic planning to the development and implementation of the blockchain solution.
Webisoft’s holistic approach to blockchain development has enabled it to deliver solutions that drive efficiency, improve transparency, and enable secure, tamper-proof transactions. The firm’s commitment to innovation, coupled with its deep understanding of the blockchain ecosystem, positions it as a leader in the blockchain development sphere.
Endnote
Zero-Knowledge Proofs (ZKPs) offer significant advantages in cost savings and user privacy. By leveraging the simplicity and efficiency of ZKPs, organizations, and individuals can protect sensitive data, streamline processes, and enhance overall security.
To fully utilize the potential of ZKPs, it is recommended to consult with our team of experts, who can provide guidance and implementation support. Don’t miss out on the opportunity to enhance privacy, reduce costs, and ensure efficient data management.
Contact our experts today to embark on a journey toward a secure and privacy-focused future.
Frequently Asked Questions
How Does Zero-Knowledge Proof Enhance Blockchain Security?
Zero-knowledge proofs provide an additional layer of security in blockchain by allowing participants to verify the accuracy of transactions or statements without exposing sensitive data.
This ensures privacy, prevents fraud, and maintains the integrity of the blockchain network.
What Are Some Practical Use Cases for Zero-Knowledge Proofs in Blockchain?
Zero-knowledge proofs have diverse applications in blockchain technology. It includes verifying digital asset ownership and conducting private transactions.
Moreover, it ensures regulatory compliance without divulging confidential information and establishes secure voting systems.
Can You Provide an Example of Zero-Knowledge Proofs in a Blockchain Scenario?
Imagine Alice wants to prove to Bob that she possesses a specific amount of cryptocurrency without disclosing the exact amount.
By employing a zero-knowledge proof, Alice can provide evidence. It convinces Bob about the validity of her claim without revealing the precise details of the amount.
Are There Any Limitations or Challenges Associated with Zero-Knowledge Proofs in Blockchain?
Although zero-knowledge proofs offer significant advantages, they also come with certain challenges.
These include the computational overhead required for generating and verifying proofs, the need for a trusted setup in certain cases, and potential vulnerabilities if the implementation is not performed correctly.