In the rapidly evolving blockchain technology world, smart contracts have emerged as a revolutionary tool, enabling agreements and trusted transactions between disparate, anonymous parties without a central authority.
However, as with any technology, smart contracts have vulnerabilities. This article delves into the intricacies of smart contract security, providing a comprehensive guide to understanding, mitigating, and preventing potential risks.
Contents
- 1 What Is A General Smart Contract?
- 2 Smart Contract’s Working Mechanism Or Function
- 3 What Is Contract Security?
- 4 Smart Contracts Security’s Prevailing Risks
- 5 Considerations For Smart Contract Security During Development Life Cycle
- 6 The Importance Of Smart Contract Security Audit
- 7 How To Perform A Smart Contract Audit?
- 8 The Process Of Smart Contract Audit
- 9 Best Practices For Smart Contract Security
- 9.1 1. Best practices for Smart Contract Security Include
- 9.2 2. Regular Audits & Penetration Testing
- 9.3 3. Adherence to the Blockchain Security Checklist
- 9.4 4. Utilization of Automatic Security Scanners
- 9.5 5. Continuous Learning And Updating Knowledge
- 9.6 6. Incorporating Security in the Development Lifecycle
- 9.7 7. Leveraging External Expertise
- 9.8 8. Building Transparency and Trust
- 9.9 9. Implementing A Bug Bounty Program
- 10 How Can Webisoft Help In Ensuring Smart Contract Security?
- 11 Conclusion: Secure Your Smart Contracts With Webisoft
What Is A General Smart Contract?
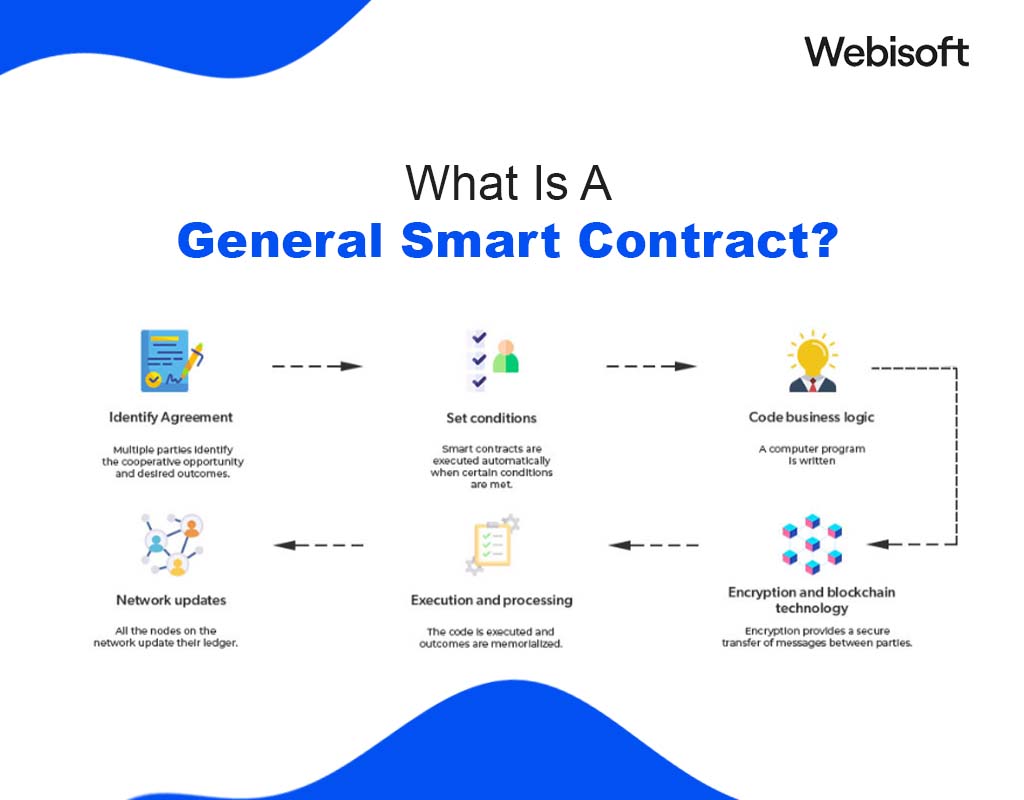
A smart contract is a digital protocol. The contract is intended to facilitate, verify, or enforce a contract’s negotiation or performance. It’s a self-executing contract with the agreement’s terms being directly written into lines of code.
The code and agreements therein exist across a distributed, decentralized blockchain network or ethereum. This code controls the execution, and transactions are trackable and irreversible, providing high transparency.
The immutability of the blockchain ensures that once a smart contract is deployed, it cannot be altered, providing a high level of security. Smart-contracts are used across a wide range of industries.
In finance, they’re used for things like decentralized finance (DeFi) applications and Initial Coin Offerings (ICOs) for security refers. In logistics, they can be used to streamline supply chains and reduce fraud. In gaming, they’re used to create and manage in-game assets.
Smart contracts’ one of the key features is their ability to be used in decentralized applications (dApps). These applications or contract smart run on the computer’s P2P network rather than a single computer.
Smart contracts serve as the transaction backbone of these dApps. Developers users using contract functions handling the business logic that controls the application’s function. In essence, smart contracts are a key building block in the new digital economy, enabling a world where every agreement, every process, every task, and every payment. Contract codes are essential for audit smart and security audit.
Smart Contract’s Working Mechanism Or Function

Smart contracts, often called crypto contracts in ethereum, are digital protocols. It facilitates, verifies, or enforces the negotiation or performance of a contract across different regions like America, Africa, Asia, Europe etc.
They are computer programs that automatically execute transactions when certain predefined conditions are met. This automation reduces the need for intermediaries and increases efficiency.
These contracts control the transfer of digital assets or currencies between parties. They provide a secure, transparent, and conflict-free way of conducting transactions on the blockchain.
All parties involved pre-set and agreed upon the transaction rules, ensuring a fair and transparent process. Every computer on the public network, also known as a node, stores these smart contracts.
This decentralized storage increases the security and reliability of the contract. It is independent of a single general point of failure and cannot be easily tampered with. The execution of smart contracts signature requires the payment of “gas” fees.
These fees are micro-transactions that compensate for the computational energy on the blockchain. One of the most important features of smart contracts is their immutability.
After deploying a smart contract to a blockchain, it cannot be altered or modified by its creators. This ensures the integrity and reliability of the AI contract, as parties can trust that the contract will execute as agreed upon, without the risk of interference or manipulation.
What Is Contract Security?

Smart contract security is a critical aspect of blockchain technology. It focuses on the safe development and interaction with smart contracts. It involves a set of principles and practices designed to protect smart contracts from potential threats, solidity and vulnerabilities.
Given the dynamic and lucrative nature of the blockchain industry, smart contracts have become a prime target for malicious actors. As such, they often face various security risks, ranging from minor bugs in the code to major vulnerabilities that could lead to significant financial losses.
Designing and deploying a smart contract comes with its own set of challenges. It requires a deep understanding of the blockchain platform it’s being deployed on and the programming language it’s written in.
Any mistake in the code can lead to unexpected behavior, making it crucial to test and audit the contract thoroughly before deployment. Operational difficulties can also arise, especially when managing and updating deployed contracts.
Since smart contracts are immutable once deployed, any necessary changes or updates require deploying a new contract. It can be a complex and resource-intensive process. Various security tools and practices are employed to mitigate these risks.
These include automated testing and auditing tools, formal verification methods, and manual code reviews. By employing these tools and adhering to best practices, developers can significantly reduce the risk of vulnerabilities and ensure their smart contracts’ safe and secure operation.
Smart Contracts Security’s Prevailing Risks

Smart contracts, despite their potential, are susceptible to various security risks. These include:
1. Oracle Manipulation
Oracles, which provide off-chain information to smart contracts, can be manipulated, leading to incorrect inputs and potential security breaches.
2. Reentrancy Attack
This occurs when functions are called repeatedly before the end of the first invocation, potentially leading to multiple withdrawals of balances.
3. Frontrunning
In frontrunning attacks, malicious users observe a pending transaction and place their transaction before it, potentially leading to financial losses.
4. Timestamp Dependence
Smart contracts that use the block timestamp function for critical logic can be manipulated, leading to potential security vulnerabilities.
5. Gas Grief
Gas griefing attacks take place when a customer sends enough gas to execute the smart contracts target but not its sub-calls, leading to uncontrolled behavior.
6. Insecure Arithmetic
Integer underflows and overflows in the Ethereum Virtual Machine (EVM) can lead to vulnerabilities that attackers can exploit.
7. Denial of Service
Denial-of-service attacks and unexpected reverts can prevent others from calling the bid function, potentially leading to financial losses.
8. Force-Feeding
Force-feeding works by forcing Ether transfer to smart contracts, potentially manipulating balance checks.
Considerations For Smart Contract Security During Development Life Cycle

The development of a secure smart contract is a journey that involves several stages. Each stage requires specific security considerations to ensure the final product is robust and free from vulnerabilities.
Let’s delve into these stages and the associated security considerations.
1. The Blueprint Stage: Designing With Security In Mind
The design phase is the blueprint stage of the smart contract development process. Developers outline the system’s features and operations, including important benchmarks. It’s crucial to consider security design and threat modeling at this stage.
Developers should establish an explicit process of identifying and prioritizing potential threats to the system at the beginning of the development cycle.
By adopting an “attacker” mindset, developers can anticipate potential vulnerabilities. And they can design the smart contract to be resilient against these threats.
2. The Building Stage: Developing Secure Smart Contracts
The development phase is where the actual coding happens. Developers create the smart contract as per the design. During this phase, it’s important to manage and update protocols to improve them by adding new features, fixing security problems, and addressing changing conditions.
However, this can be a safety and security risk if the ability to upgrade needs to be properly controlled. Access control can be used to restrict special functions that perform administrative tasks.
Developers should use existing smart contract standards if possible. And they should assess the security assumptions that protocol integrations might require.
3. The Inspection Stage: Testing and Reviewing for Security
The testing and review phase is the inspection stage, where developers evaluate the smart contract in a testing environment. They assess the smart contract’s correctness, scale, and other factors.
It also encourages threat models related to deeper thought. An internal code review for bug detection and an external audit should take place before production deployment.
4. The Launch Stage: Deploying and Maintaining Secure Smart Contracts
The deployment and maintenance phase is the launch stage, where the smart contract is deployed in the production environment. After deployment, developers evaluate and modify the system to ensure it performs its intended functions.
Developers should also encourage the community’s development of protocol-monitoring detection robots. Regular audits and pen testing should be conducted even after the smart contract has been deployed to ensure ongoing security.
The Importance Of Smart Contract Security Audit

In smart contract development, security is not an afterthought but an integral part of the process. This journey is often referred to as the smart contract development life cycle.
It involves several stages, each with its unique security considerations. Let’s delve into each phase and explore the security aspects that need attention.
1. Design Phase: Laying the Foundation of Security
The design phase is the blueprint stage, where developers outline the system’s features and operations. It’s crucial to incorporate security design and threat modeling at this stage.
Developers need to adopt an “attacker” mindset and assume potential vulnerabilities. All security assumptions should be clearly stated, and the process of identifying and prioritizing potential threats should be established.
Engaging security consultants in the early design phase can be beneficial if the team lacks security expertise.
2. Development Phase: Building with Security in Mind
During the development phase, developers create the code as per the design. Using existing smart contract standards whenever possible is essential to reduce security risks.
Developers should also assess the security risks associated with protocol integrations. And they develop security checks to prevent attacks on external components. Access control can be used to restrict special functions that perform administrative tasks.
3. Testing and Review Phase: Checking for Security Flaws
The testing and review phase involves evaluating all modules in a testing environment to assess their correctness, scale, or other factors. Developers should create assumptions about the codebase’s expected behavior. They want to ensure that threat models are being addressed.
A code’s test suite can be used to verify or disprove development assumptions. It’s crucial to create clear and comprehensive documentation about the code and set up an easy-to-use, fast-running test suite.
4. Deployment and Maintenance Phase: Ensuring Ongoing Security
Once the smart contracts are deployed, the maintenance phase begins. Regular audits and pen-testing are necessary even if the system seems flawless.
By incorporating security measures at every stage, developers can ensure the creation of secure and reliable smart contracts.
How To Perform A Smart Contract Audit?

Smart contract audits are a critical aspect of the blockchain ecosystem. They ensure the security and reliability of smart contracts, which are the backbone of many blockchain applications. Here’s a detailed guide on how to perform a smart contract audit:
1. Manual Auditing: A Deep Dive into the Code
Manual auditing is a meticulous process where experts scrutinize each line of code. This method is highly effective in identifying potential issues, as it allows for a deep understanding of the smart contract’s logic and functionality.
The auditors look for any code anomalies, potential security vulnerabilities, and adherence to coding standards. They also assess the smart contract’s functionality against its intended behavior.
2. Automated Auditing: Speed and Efficiency
Automated auditing complements manual auditing using software tools to scan the smart contract code for common vulnerabilities. These tools can quickly analyze large codebases, providing a broad overview of potential issues.
However, they may need help understanding the context and could miss certain vulnerabilities. Therefore, automated auditing should be used with manual auditing for a comprehensive audit.
The Audit Process: A Step-by-Step Guide

- Collection of Code Design Models: The auditors gather the code specifications. Also they inspect the architecture to ensure third-party smart contract integration. This step helps auditors understand the project’s scope and goals.
- Running Unit Tests: Auditors use automated and manual tools to test each smart contract function. This ensures that the unit test cases cover the entire smart contract code.
- Choosing the Auditing Method: Depending on the project’s requirements, auditors may opt for manual, automated, or a combination of both methods.
- Preparing the Initial Report: After the audit, the auditors draft a report detailing any code flaws found and provide feedback to the project team.
- Publication of the Final Audit Report: Reporters or auditors publish the final report after fixing the identified bugs. Fixing the bugs includes any actions the project team members and external experts took to address the issues.
Remember, the process may vary slightly based on the auditors’ methodologies and the specific requirements of the smart contract. However, the core principles remain the same: thorough examination and identification of vulnerabilities.
The Process Of Smart Contract Audit

The process of auditing a smart contract is meticulous, involving several key steps to ensure the security and functionality of the contract. Here’s a more detailed breakdown of the process:
1. Gathering Code Design Models
The first step in the audit process involves the collection of code design models. This allows auditors to understand the project’s scope and objectives comprehensively.
It also provides insight into the architecture of the smart contract, which is crucial for identifying potential vulnerabilities.
2. Running Unit Tests
Once the code design models have been collected, auditors run unit tests on each smart contract function.
This is done using both manual and automated tools to make sure that the unit test cases cover the entire code of the smart contract. This step is crucial for identifying potential issues or vulnerabilities in the contract’s functions.
3. Choosing the Preferred Auditing Method
After running the unit tests, auditors decide on the most suitable auditing method. This could be either manual or automated auditing. Manual auditing involves a team of experts reviewing each line of code to identify potential issues.
On the other hand, automated auditing uses bug detection software to locate errors. Both methods have advantages and should be used to ensure comprehensive coverage.
4. Preparing the Initial Report
Once the auditing is complete, auditors prepare an initial report detailing any flaws found in the code. This report is then shared with the project team for review.
It’s important to note that smart contract service providers often have a team to fix any bugs identified during the audit.
5. Publishing the Final Audit Report
The final step in the audit process involves publishing the final audit report. This report includes any actions the external experts and project team took to address the issues identified in the initial report.
The final report serves as a comprehensive document detailing the security and functionality of the smart contract. The process of auditing a smart contract is meticulous and requires a high level of expertise and attention to detail.
By following these steps, auditors can ensure the security and functionality of smart contracts. Thereby they protect the investments made through them.
Best Practices For Smart Contract Security

1. Best practices for Smart Contract Security Include
- Regular audits and pen testing.
- Following the blockchain security checklist.
- Running an automatic security scanner.
These practices help identify and prevent systemic flaws, build trust between investors and end-users, and facilitate risk assessment and mitigation.
2. Regular Audits & Penetration Testing
- Regular audits and penetration testing are crucial for maintaining smart contract security. This process involves thoroughly examining the system to identify vulnerabilities that hackers could exploit.
- Even if the system appears secure, conducting these checks regularly is essential, as new vulnerabilities can emerge over time.
- Regular audits provide an opportunity to address these vulnerabilities before they can be exploited, thereby enhancing the overall security of the smart contract.
3. Adherence to the Blockchain Security Checklist
- Following a comprehensive blockchain security checklist is another best practice for ensuring smart contract security.
- This checklist may include enforcing multi-factor authentication, implementing security incident and event management (SIEM), and establishing policies that determine the appropriate level of access.
- By adhering to this checklist, developers can ensure they take all necessary steps to secure their blockchain applications.
4. Utilization of Automatic Security Scanners
- Automatic security scanners can help identify security flaws in smart contracts. These scanners can analyze the code and highlight potential vulnerabilities, allowing developers to address these issues proactively.
- These scanners can provide detailed information about the vulnerability, the components affected, steps to fix the issue, and the potential impact of the vulnerability.
- By regularly running an automatic security scanner, developers can maintain a high level of security in their smart contracts.
5. Continuous Learning And Updating Knowledge
- The field of blockchain and smart contract security is continuously evolving. Therefore, developers must stay updated with the latest security trends, vulnerabilities, and mitigation strategies.
- This can be achieved through regular training, attending relevant workshops and seminars, and staying informed about the latest research in the field.
6. Incorporating Security in the Development Lifecycle
- Security should not be an afterthought in the development process. Instead, it should be incorporated at every stage of the development lifecycle.
- Security considerations should be integral to the process from the design phase to the deployment and maintenance phase. This approach ensures that security is not just a one-time activity but a continuous effort throughout the lifecycle of the smart contract.
7. Leveraging External Expertise
- Sometimes, it can be beneficial to leverage external expertise through security consultants or auditors. These experts can provide a fresh perspective and may be able to identify vulnerabilities that the internal team might have missed.
- They can also provide valuable advice on the best security practices and help improve the overall security posture of the smart contract.
8. Building Transparency and Trust
- Transparency is key to building trust with users. This can be achieved by making the smart contract code open source, which allows anyone to review the code and verify its security.
- Additionally, regular communication about the security measures in place and the results of security audits can help build trust with users and stakeholders.
9. Implementing A Bug Bounty Program
- A bug bounty program encourages independent researchers to find and report vulnerabilities in the smart contract in exchange for a reward.
- This can be an effective way to identify and fix security issues, as it leverages the collective expertise of the cybersecurity community.
By following these best practices, developers can enhance the security of their smart contracts, thereby protecting the interests of all stakeholders involved.
How Can Webisoft Help In Ensuring Smart Contract Security?
Webisoft can help ensure your smart contract security through its smart contract auditing service and smart contract monitoring tool. Their auditing service includes automated and manual testing to identify and address any vulnerabilities in your source code.
Their smart contract monitoring tool provides a web-based platform to view details about smart contracts and their transactions. It sends real-time alerts on various events and helps protect contracts by detecting and alerting suspicious activity or errors.
Conclusion: Secure Your Smart Contracts With Webisoft
Smart contract security is a critical aspect of blockchain technology that cannot be overlooked. By understanding the potential risks and implementing the necessary security measures, you can ensure the integrity and reliability of your smart contracts.
Webisoft’s smart contract auditing service and smart contract monitoring tool can provide the comprehensive security coverage you need to protect your investments and build trust with your users. Secure your future with Webisoft today.