How to Create a Private Blockchain Network: A Complete Guide
- BLOG
- Blockchain
- October 12, 2025
By 2030, private blockchains are projected to add over $1 trillion in business value. That’s huge, but here’s the catch: most businesses still struggle to figure out how to build one without getting lost in jargon or high costs. So, how to create a private blockchain network? The process involves setting the rules, configuring nodes, choosing consensus, managing permissions, and deploying smart contracts.
Sounds simple, yet without the right plan, these steps can feel overwhelming. This guide is your shortcut. You’ll get a step-by-step roadmap, practical advice, and insider tips on avoiding mistakes. By the end, you’ll know exactly how to create a private blockchain network that works for your business.
Contents
- 1 What Is a Private Blockchain Network?
- 2 Reasons Businesses Choose to Build a Private Blockchain Network
- 3 Build Your Private Blockchain Network With Webisoft Experts!
- 4 How to Create a Private Blockchain Network: Step-by-Step
- 4.1 Step 1: Define Your Goals and Platform
- 4.2 Step 2: Prepare the Infrastructure
- 4.3 Step 3: Define the Genesis Block
- 4.4 Step 4: Set the Consensus Mechanism
- 4.5 Step 5: Create and Connect Nodes
- 4.6 Step 6: Define Permissions and Identities
- 4.7 Step 7: Deploy Smart Contracts or Chaincode
- 4.8 Step 8: Enable Monitoring and Security
- 4.9 Step 9: Maintain and Scale
- 5 Security Essentials for Private Blockchain Networks
- 6 How to Integrate a Private Blockchain Network with Existing Systems
- 7 Mistakes to Avoid When Creating Private Blockchain Network
- 8 Work with Webisoft: Enterprise Experts in Private Blockchain Development
- 9 Build Your Private Blockchain Network With Webisoft Experts!
- 10 Conclusion
- 11 Frequently Asked Question
What Is a Private Blockchain Network?
A private blockchain network is a permissioned blockchain system where only verified members such as enterprises, agencies, or consortium partners can join, validate transactions, and access data. It operates under controlled governance, ensuring privacy, compliance, and accountability among trusted participants.
Unlike public blockchains, private networks restrict access but retain core features like cryptographic linking and tamper-evident records. They use efficient consensus mechanisms, enabling faster validation, scalability, and secure collaboration within a closed, trusted environment.
How Private Blockchains Retain “Blockchain Qualities” Even Without Public Access
 Although private blockchains operate in closed, permissioned environments, they still preserve the essential properties that define blockchain technology
Although private blockchains operate in closed, permissioned environments, they still preserve the essential properties that define blockchain technology
Immutability & Tamper-Evidence
Each block is cryptographically linked to the previous one, making unauthorized changes immediately detectable. Some networks enhance this by anchoring state hashes to public blockchains (state pinning), adding external, time-stamped proof of integrity without exposing private data.
Distributed Agreement (Consensus)
Validation doesn’t depend on public mining. Instead, private chains use efficient models such as Raft (CFT), IBFT/QBFT/PBFT (BFT), Proof of Authority, or Tendermint. This enables fast, secure agreement among verified participants without requiring every node’s approval.
Auditability Within Scope
All transactions, configuration updates, and governance actions are logged in tamper-evident records accessible to authorized parties. Some frameworks provide read-only or auditor nodes, while platforms like Corda use Notaries to ensure transaction uniqueness and prevent double-spending without exposing sensitive business data.
Reasons Businesses Choose to Build a Private Blockchain Network
Enterprise investment in blockchain is booming in 2025 alone, spending reached US $11.7 billion, with much of it directed at private and permissioned networks. Businesses choose them for several reasons:
- Control & Permissioning: You define exactly who can join, validate transactions, and view data. This tight control is crucial for industries handling sensitive records.
- Regulatory Compliance: Frameworks like GDPR or HIPAA can be built directly into the system, ensuring that compliance is automatic while avoiding public exposure.
- Data Confidentiality: Information can be restricted by role, so confidential records or trade secrets remain visible only to those who need access.
- Collaboration & Trust: Suppliers, partners, and regulators can operate on one shared ledger, creating a single source of truth without risking outside visibility.
For more context, check these real-world blockchain applications that show how businesses are already applying blockchain in practice.
- Cost & Efficiency Gains: Smart contracts reduce paperwork, eliminate intermediaries, and minimize human error, cutting costs while speeding up processes.
Build Your Private Blockchain Network With Webisoft Experts!
Get secure, scalable blockchain solutions designed to fit your business needs.
How to Create a Private Blockchain Network: Step-by-Step
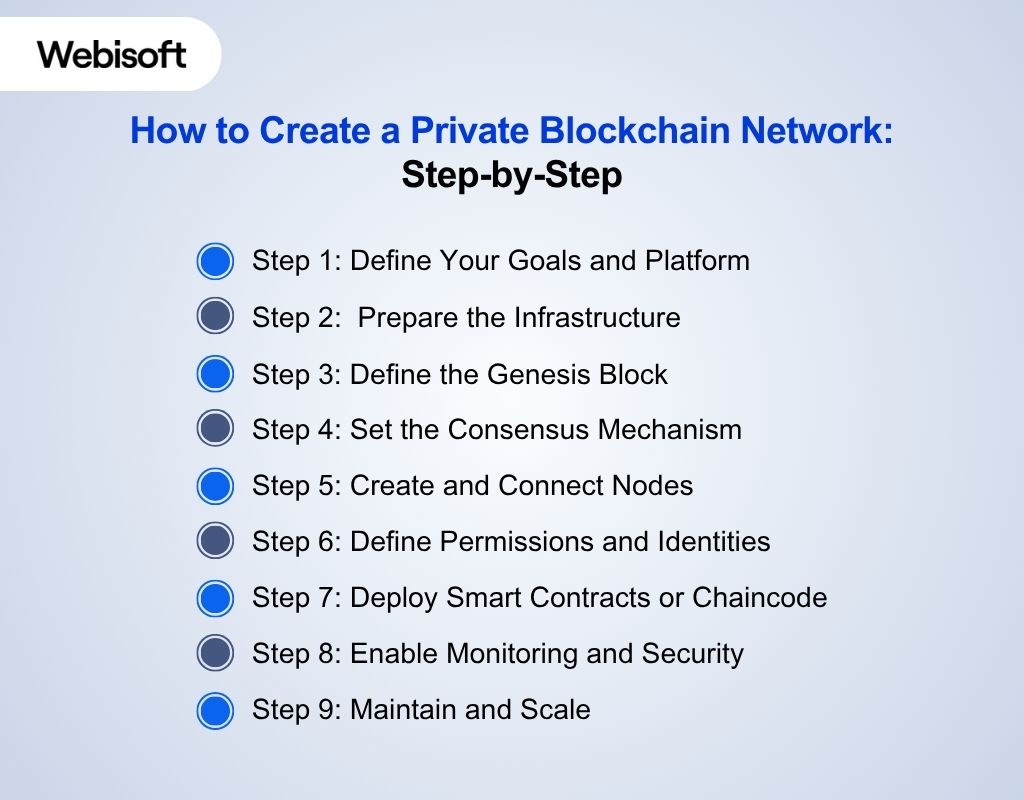 Building a private blockchain network requires clear planning, the right tools, and structured execution. Follow these step-by-step instructions to design, deploy, and manage your secure system.
Building a private blockchain network requires clear planning, the right tools, and structured execution. Follow these step-by-step instructions to design, deploy, and manage your secure system.
Step 1: Define Your Goals and Platform
Start with your objectives and governance model. Determine the trust level, data visibility, and regulatory requirements your network must meet. Choose your privacy model: selective data sharing with Hyperledger Fabric, encrypted private transactions in Quorum/Besu, or point-to-point communication in Corda. Clarify your business use case, finance, supply chain, or healthcare and the compliance standards it must follow (GDPR, HIPAA, or ISO). Decide the technology fit:
- Hyperledger Fabric → modular design with channels and private data collections.
- Quorum/Besu → Ethereum-based with Tessera for private transactions.
- Corda → financial-grade with Notaries ensuring transaction uniqueness.
- Tendermint/Substrate → customizable BFT-based chains. For added tamper-proofing, consider anchoring state hashes to a public blockchain, a method known as state pinning.
Step 2: Prepare the Infrastructure
A strong and secure infrastructure is the backbone of any private blockchain network.
- Deployment Model: Choose between on-premises, cloud, or hybrid environments based on scalability, compliance, and control needs.
- Network Topology:
- Set up private subnets for validators, orderers, notaries, and privacy managers.
- Use bastion hosts for controlled ingress and firewalls for node isolation.
- Segment networks by organization or region for higher security and performance.
- Orchestration: Deploy nodes with Kubernetes or Docker for container management, auto-scaling, and rolling upgrades.
- PKI & Key Management:
- Implement root and intermediate Certificate Authorities (CAs) for identity verification.
- Use Hardware Security Modules (HSMs) or cloud Key Management Services (KMS) for secure key storage and rotation.
- Databases:
- Hyperledger Fabric → LevelDB (default) or CouchDB (for richer queries).
- Corda → PostgreSQL, Oracle, or SQL Server for reliable persistence.
- System Hardening: Apply OS-level security patches, enforce mutual TLS (mTLS), and follow least-privilege access principles.
- Monitoring & Observability:
- Use Prometheus + Grafana for metrics and visualization.
- Implement centralized logging and alerting to track node activity and detect anomalies.
- Backup & Disaster Recovery:
- Maintain off-site backups of ledgers, configurations, and keys.
- Use snapshotting and failover drills to test recovery and business continuity.
Step 3: Define the Genesis Block
Every blockchain starts with a genesis block, the first block that sets the rules for the entire chain. For a practical walkthrough, see the official docs on Ethereum private networks that explain how to configure genesis blocks and nodes.
- Configure chain ID, difficulty, and block parameters.
- Establish the initial participants and their roles.
- Ensure every node uses the same genesis configuration so they operate on the same network.
In Fabric, set channel configurations and Raft orderer policies. In Corda, define Network Parameters and bootstrap via CENM components (Doorman, Network Map, Notary).
Step 4: Set the Consensus Mechanism
Consensus determines how nodes agree on valid transactions. Private blockchains use efficient, fault-tolerant protocols instead of energy-intensive mining:
- Proof of Authority (PoA) → trusted validators confirm blocks rapidly; variants include Clique and enterprise-grade QBFT.
- Crash Fault Tolerant (CFT) → Raft (used in Fabric) offers fast, leader-based replication in trusted environments.
- Byzantine Fault Tolerant (BFT) → IBFT 2.0, QBFT, or PBFT tolerate malicious nodes and ensure finality when ≥ 2/3 validators agree.
- Tendermint → PBFT-style rounds with fast finality; ideal for modular chains.
- Corda Notary clusters → guarantee transaction uniqueness; can operate in CFT or BFT mode.
Select your model based on validator trust, latency, and scalability goals, and configure validator rotation and quorum thresholds.
Step 5: Create and Connect Nodes
Deploy multiple nodes, validators, peers, or observers and configure peer-to-peer connectivity with static peers or bootnodes. Enable mutual TLS for all connections and verify that nodes sync correctly. Test for consensus stability, block propagation, and ledger consistency under load.
Step 6: Define Permissions and Identities
Set fine-grained access control: ☐ Read data ☐ Submit transactions ☐ Validate blocks Use digital certificates or identity management systems for authentication.
- In Fabric, define Membership Service Providers (MSPs) and channel policies.
- In Quorum/Besu, configure basic or enhanced permissioning for nodes and accounts.
- In Corda, onboard members via the Doorman and Network Map.
Step 7: Deploy Smart Contracts or Chaincode
Develop and test smart contracts, Solidity for EVM networks, Go/Java for Fabric, and Kotlin/Java for Corda. Use controlled deployment pipelines with peer review, automated testing, and versioning.
Deploy contracts to automate workflows and enforce business logic. If you want to know in-depth, our guide on blockchain application creation explains how these smart contracts evolve into full applications.
Step 8: Enable Monitoring and Security
Set up dashboards for validator health, transaction throughput, and latency. Apply strong security measures, TLS encryption, HSM-backed keys, immutable audit logs, and hardened infrastructure.
Step 9: Maintain and Scale
- Add new nodes or participants as your network grows.
- Roll out software updates and protocol changes through agreed governance rules.
- Following a proper software release lifecycle process helps keep upgrades smooth, predictable, and secure for your blockchain network.
- Run periodic load tests to ensure the network meets performance targets.
Need expert guidance? Book a consultation with Webisoft now and let our team build a secure, private blockchain customized to your business. Image Idea: Infographic flow showing 9 steps: Goals and Platform → Infrastructure → Genesis Block → Consensus → Nodes → Permissions → Smart Contracts → Security → Scaling.
Security Essentials for Private Blockchain Networks
When you build a private blockchain, security isn’t optional, it’s foundational. In fact, knowing how to create a private blockchain network starts with securing these essentials.
- Identity & Certificate Management – Every participant and node must have a verifiable digital identity issued by a trusted authority, ensuring full accountability.
- Key Management with HSMs – Store cryptographic keys in hardware security modules, enforce regular rotation, and separate duties to eliminate single points of failure.
- Mutual TLS Encryption – Encrypt all communication between nodes and users with mTLS, preventing interception, spoofing, or tampering.
- Granular Access Control – Define precise roles and permissions for validators, peers, and administrators. No default or blanket privileges.
- Private Data Channels – Use subnets, private channels, or collections so sensitive data is only shared with authorized participants, not the entire network.
- Resilient Consensus – Deploy consensus algorithms that maintain integrity even if nodes are faulty or compromised, protecting the ledger from corruption.
- Immutable Audit Logs – Capture and preserve detailed records of membership changes, node activity, and policy updates in tamper-evident form.
- Node Hardening – Secure the underlying infrastructure with hardened OS configurations, container security, firewalls, and intrusion detection systems.
- Governance Controls – Codify rules for membership changes, software upgrades, and policy updates to keep the network predictable and secure.
How to Integrate a Private Blockchain Network with Existing Systems
Once your blockchain is secure, the next step in how to create a private blockchain network is integration. Connecting it with databases, ERPs, or CRMs ensures it adds real value, not just isolation.
Key Steps & Practical Tips for Integration

- Map Data Flows & Integration Points
Identify which systems will push or receive data from blockchain (ERP, CRM, file stores). Understand data formats, frequency, volume.
- Use Middleware or APIs for Interoperability
Often you’ll need a layer that translates between your old systems and the blockchain. APIs or adapters let you connect without rewriting everything.
- Maintain Data Consistency
When old systems and blockchain both store similar data, sync them properly. Use mechanisms like event-driven updates or scheduled reconciliation.
- Ensure Compatible Identity & Permissions
If you already have user or identity systems, map their roles into your blockchain permissions. Use the same authentication where possible to reduce friction.
- Handle Data Privacy & Compliance
Not all data belongs on the blockchain. Decide what stays off-chain, what is private vs shared. Be compliant with laws (GDPR, etc.).
- Plan for Transaction Latency & Performance
Existing systems may expect very fast responses. Blockchain adds overhead. Test performance impact and optimize where possible (e.g. batch transactions).
- Test Thoroughly in a Staging Environment
Before going live, simulate integration: test data flows, permission checks, failures. You want to catch mismatches early.
Mistakes to Avoid When Creating Private Blockchain Network
Launching a private blockchain isn’t just about setup. Many projects fail because of avoidable missteps. When learning how to create a private blockchain network, keep an eye out for these common mistakes:
- Using blockchain where it isn’t needed → Don’t force it; sometimes a database is enough.
- Skipping stakeholder alignment → If legal, compliance, or operations aren’t onboard, expect roadblocks later.
- Ignoring upgrade paths → Plan how you’ll update nodes, add participants, or change protocols.
- Underestimating integration complexity → Data formats, latency, and version mismatches can break workflows.
- Scaling too early → Test small first; premature scaling creates bottlenecks.
- Overlooking skill gaps → Train your team or bring in experts to avoid costly mistakes.
- No audit or recovery plan → Without monitoring and backups, one failure can take down the whole network.
Work with Webisoft: Enterprise Experts in Private Blockchain Development
 You deserve a partner who goes beyond blockchain theory with real-world experience. Webisoft delivers secure, custom private blockchain networks aligned with your enterprise goals.
You deserve a partner who goes beyond blockchain theory with real-world experience. Webisoft delivers secure, custom private blockchain networks aligned with your enterprise goals.
- Purpose-Built Architectures: We don’t just set up blockchains, we engineer networks around your organization’s governance, transaction flows, and compliance requirements.
- Advanced Permissioning Models: Role-based and multi-tier access ensures data can be shared across departments or partners with precision, without overexposure.
- Enterprise-Grade Performance: Consensus algorithms are optimized for low latency and high throughput, supporting mission-critical applications like supply chain, finance, and healthcare.
- Interoperability Without Risk: Private networks can be isolated for confidentiality, but also bridged with public chains when business models require settlement or tokenization.
- Seamless Integration: Our private blockchains connect with ERP, CRM, cloud, and legacy systems to minimize disruption and accelerate adoption.
- Proven ROI: Clients use private blockchain networks to reduce reconciliation costs, increase traceability, automate settlement, and build trust across closed ecosystems.
Build Your Private Blockchain Network With Webisoft Experts!
Get secure, scalable blockchain solutions designed to fit your business needs.
Conclusion
By now, you know that how to create a private blockchain network is less about theory and more about execution. Success depends on careful planning, smart technology choices, and a clear roadmap that avoids pitfalls.
When executed well, your network becomes a secure foundation for innovation and growth. With Webisoft, you don’t have to navigate this alone. Book a free consultation today and let our experts turn your blockchain vision into a reliable, scalable network built for your business goals.
Frequently Asked Question
How long does it take to build a private blockchain network?
To build a private blockchain network depends on complexity and requirements. A simple proof-of-concept may take 4–8 weeks, while a full enterprise-grade deployment with integrations, governance, and testing can extend to 6–12 months.
Can a person own a private blockchain?
Yes, private blockchains can be owned and controlled by an individual or organization. Unlike public blockchains, they are permissioned, meaning the owner decides who can join, validate, and access information, ensuring authority and governance remain centralized.
Do private blockchains use cryptocurrency?
Not always. Private blockchains often operate without a native cryptocurrency, since all participants are verified. However, tokens may be added for internal purposes, such as value transfers, supply chain tracking, or incentivizing participants, depending on the business model.


